- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
Detecting PwnKit (CVE-2021-4034) Using Trend Micro™ Vision One™ and Cloud One™

Exploits & Vulnerabilities
This blog discusses how CVE-2021-4034 can be detected and blocked using Trend Micro™ Vision One™ and Trend Micro Cloud One™.
Read time: ( words)
PolKit, or PolicyKit, is a component that handles system-wide policies and authorizations in Unix and Unix-like operating systems (OS), allowing non-privileged processes to communicate with privileged ones. PolKit’s pkexec comes bundled in major Linux distributions, a tool generally used to execute commands with elevated privileges (root capabilities). The component also enables an authorized user to execute programs as another user (generally ‘root’). The function is synonymous to ‘runas’ in Windows.
Security researchers disclosed PwnKit as a memory corruption vulnerability in polkit’s pkexec, assigned with the ID CVE-2021-4034 (rated High at 7.8). The gap allows a low-privileged user to escalate privileges to the root of the host. Various proofs of concept have been disclosed, written in different languages (such as several in C, Python, Bash, and Go), and the vulnerability has been there for over 12 years, affecting all versions of the pkexec since its first distribution in 2009.
These make the security gap “an attacker’s dream come true” and a vulnerability that needs to be fixed as soon as possible: Any unprivileged local user can abuse this to get full root privileges and exploit the gap even if the polkit daemon itself is not running. Attackers can reintroduce environment variables in the context of the ‘pkexec’ binary, leading to a controlled execution of an attacker-controlled shared library and gaining code execution with ‘root’ privileges. Security teams are advised to patch this as soon as possible, or to apply temporary mitigation steps while updating their respective systems. This blog discusses how Trend Micro™ Vision One™ and Trend Micro™ Cloud One™ can be used to detect the abuse of the said vulnerability.
Trend Micro Cloud One™ – Workload Security
Using the platform of Trend Micro Cloud One – Workload Security, the following modules can be used to detect the abuse of CVE-2021-4034:
1. Activity Monitoring: This module can detect process, file, and network activities on endpoints running Cloud One Workload Security. In this case, we will look into the process and file activities since there is no network component to this attack scenario.
2. Anti-malware: This module provides protection against the exploitation of this vulnerability in real time using behavior monitoring.
3. Log Inspection: This module can tap in the authentication-related events on the host. When the proof of concept is executed, there are observations on /var/log/auth.log from where we can deduce suspicious activity with respect to pkexec. The 1002831 – Unix – Syslog Log Inspection rule can potentially detect the exploitation of CVE-2021-4034.
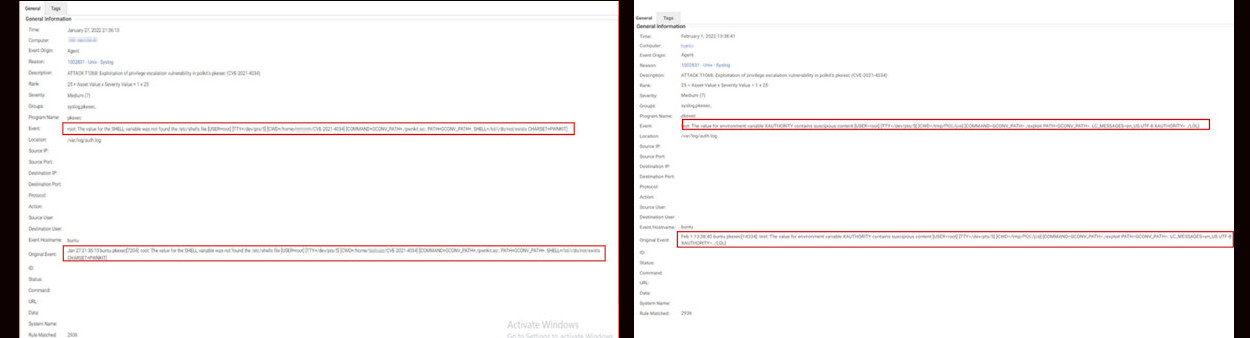
Trend Micro Vision One
Trend Micro Cloud One – Workload Security’s correlation of telemetry and detections provide initial security context, allowing security teams and analysts to track and monitor the threats that may abuse CVE-2021-4034. In the next section, Trend Micro Vision One provides more details into the paths and events in real time.
Observed attack techniques (OATs)
Observed attack techniques (OATs) are generated from individual events that provide security value. To look into the possible attempts of exploitation using this vulnerability, we can look for these OAT IDs from many other helper OAT triggers that indicate suspicious activities on the buntu host.
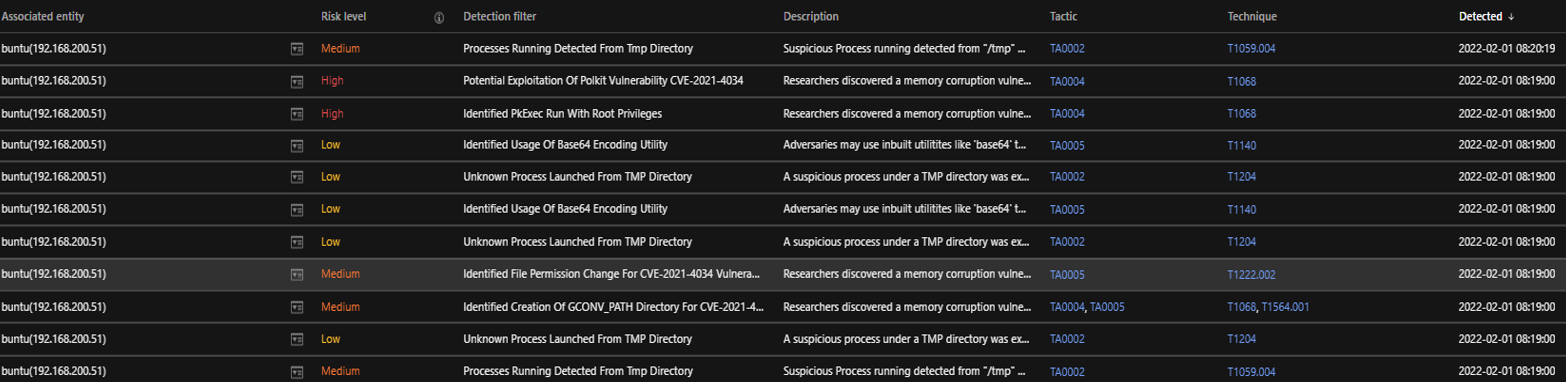
The following OAT IDs can be used while threat hunting:
- F2533 – Identified File Permission Change For CVE-2021-4034 Vulnerability Exploitation
- F4875 – Identified Creation Of GCONV_PATH Directory For CVE-2021-4034 Vulnerability Exploitation
- F4880 – Identified PkExec Run with Root Privileges
- F4873 – Potential Exploitation of Polkit Vulnerability CVE-2021-4034
- F4881 – Potential PwnKit CVE-2021-4034 Exploitation Traces Logged
Root cause analysis (RCA)
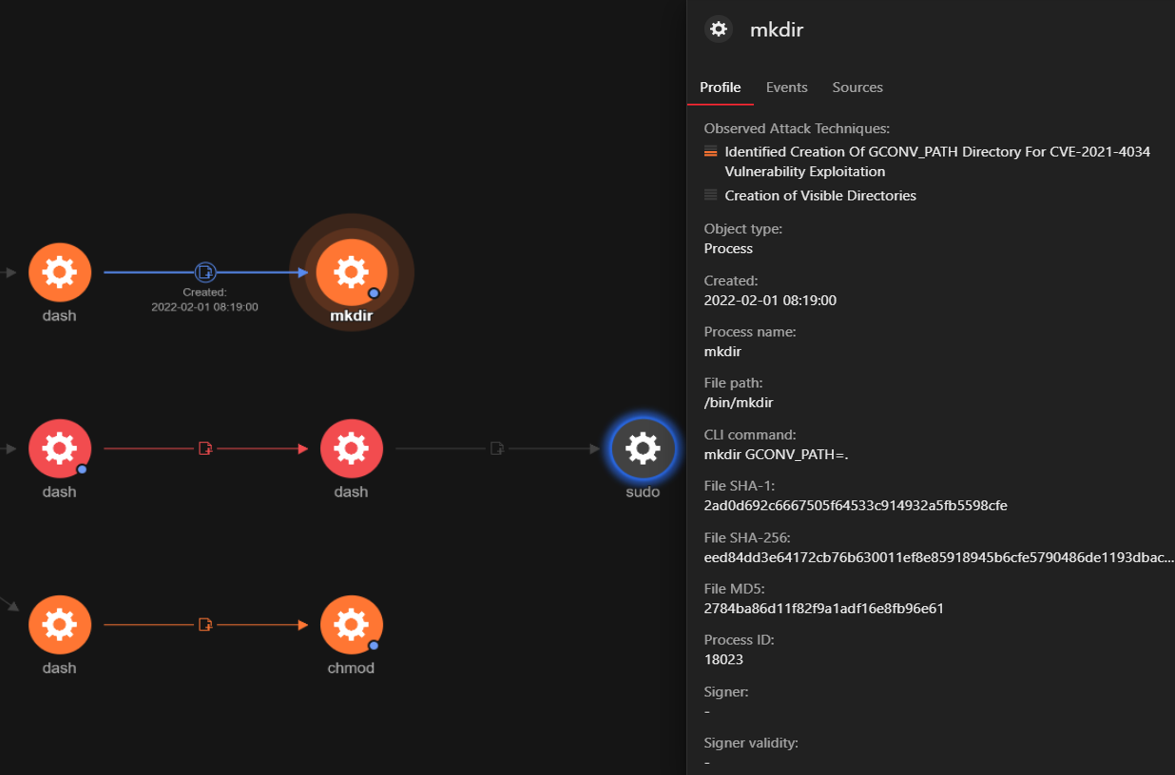
Execution Profile is a feature in Vision One that generates graphs for security teams. We can expand this for fields like ‘processCmd’ or ‘objectCmd’ from the search or threat hunting apps for activities observed within a given time frame such as process creation, file creation, and inbound and outbound network activity, among other parameters. Threat hunters and security analysts can expand the initial hypothesis to figure out the execution details and sequence using RCAs shown in this section. For this vulnerability, we have observed the following operations:
a. Creation of a directory with the name ‘GCONV_PATH=.’
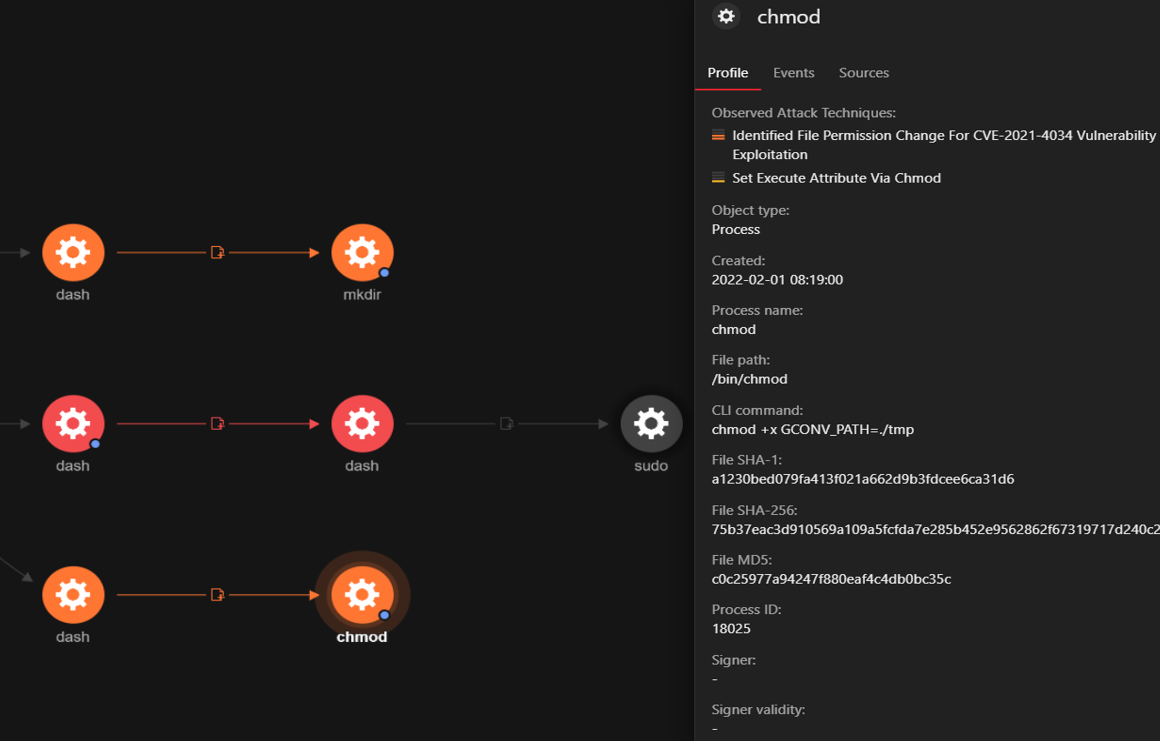
b. Change of permissions for a random file in ‘GCONV_PATH=.’ Directory
c. Execution of ‘pkexec’ as the ‘root’ user from a non-root parent
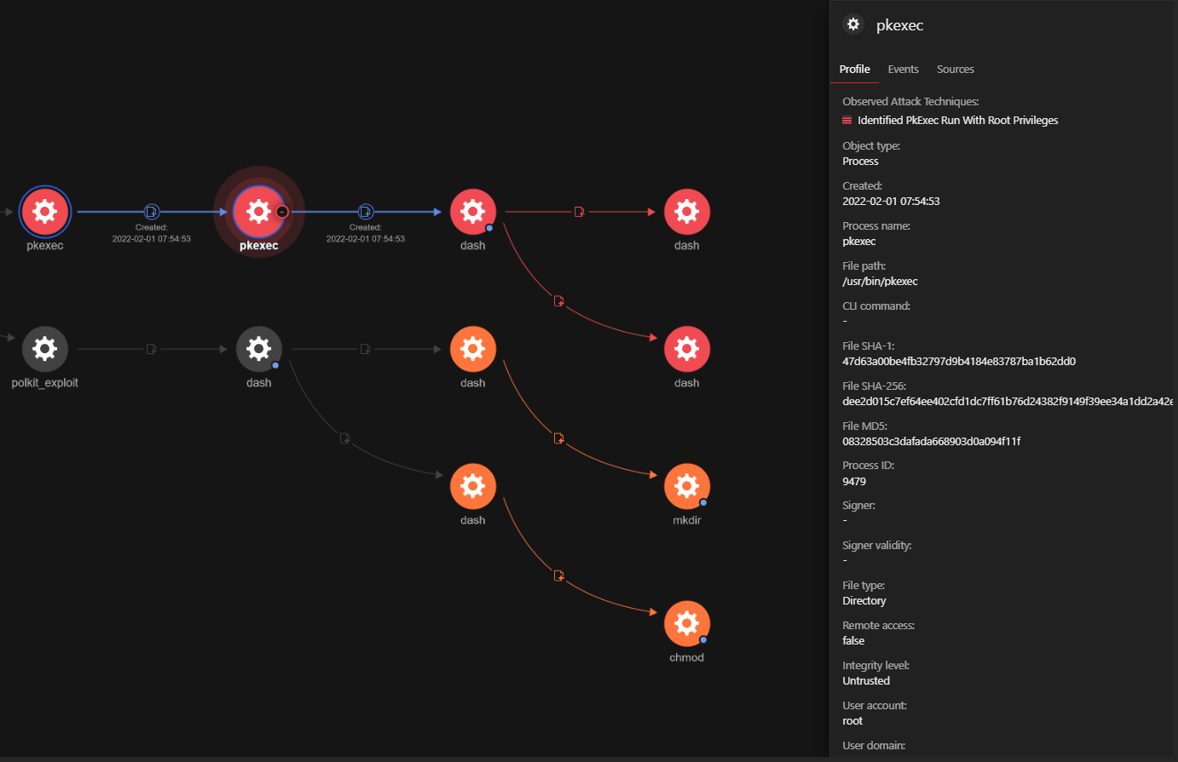
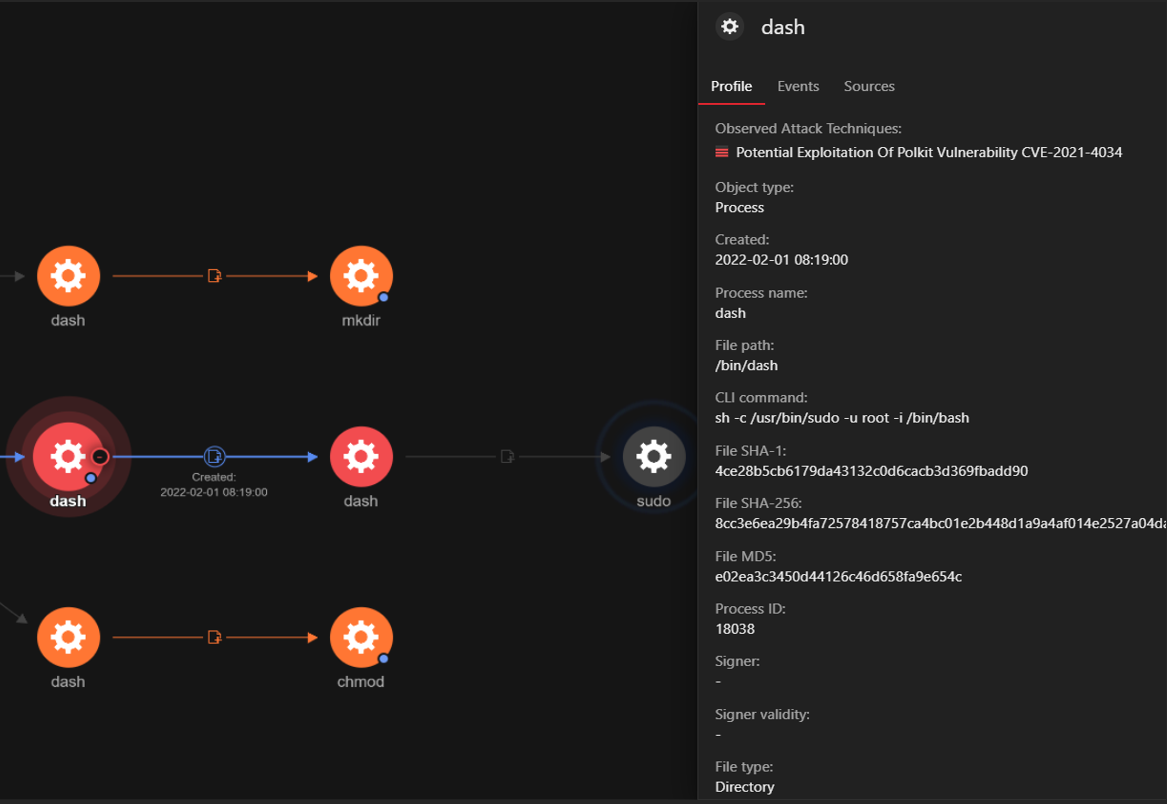
d. Launch of a shell from ‘pkexec’ as the parent process
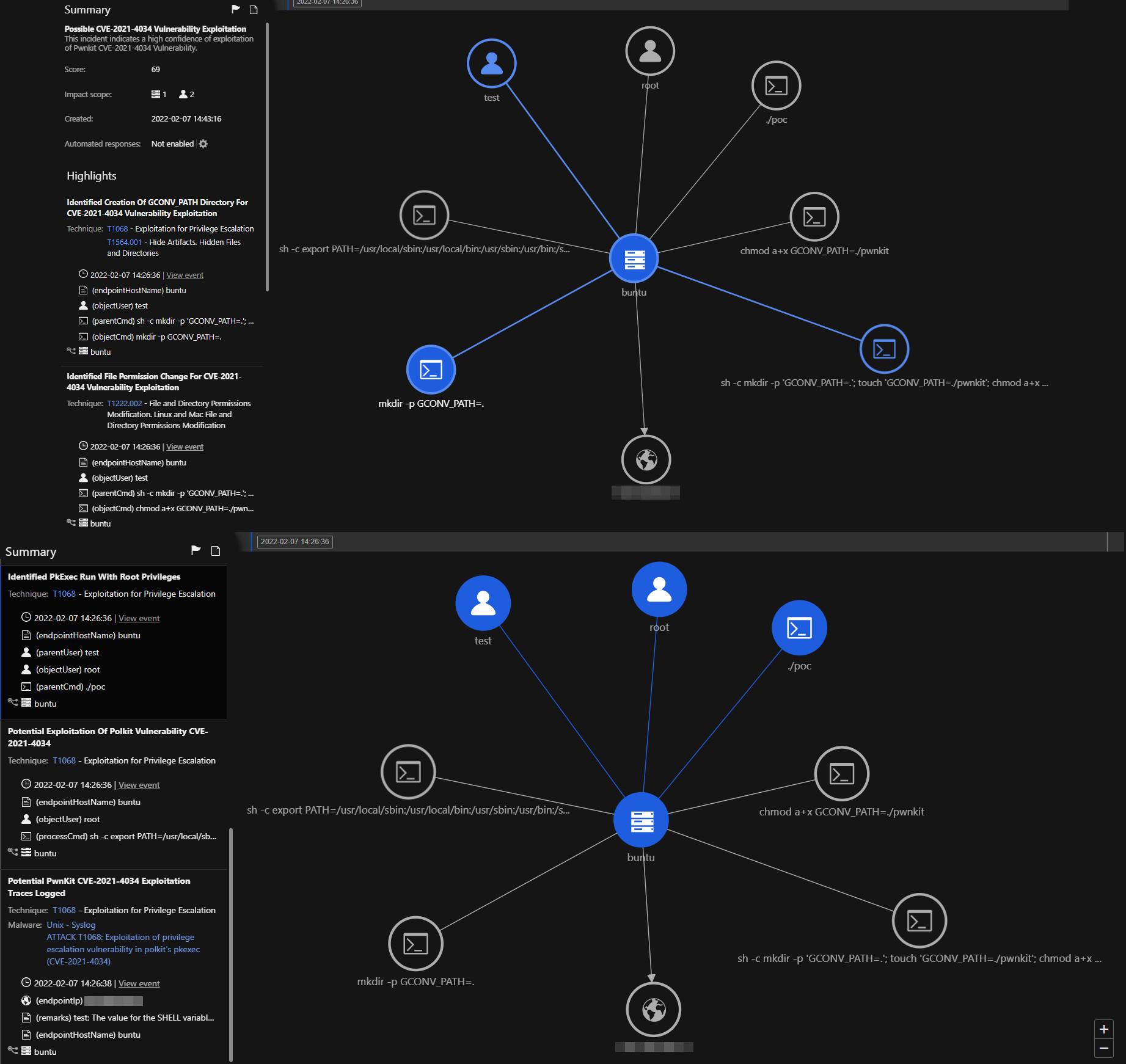
Trend Micro Vision One Workbench App
The Trend Micro Vision One Workbench app helps analysts see the significant correlated events intelligently based on occurrences throughout the entire fleet of workloads. The left side of the diagram shows the summarized sequence of events happening one after the other. Analysts can view the different fields of interest that are considered important and provide security value on the right. The app allows security teams to see the compromised assets and isolate those that can be potentially affected while patching procedures are in progress.
Conclusion
Based on our tests, companies’ security teams can execute a manual workaround by checking for the following strings in the /var/log/auth.log file:
- “The value for the SHELL variable was not found the /etc/shells file”
- “The value for environment variable * contains suspicious content,” wherein * can be anything like SHELL or XAUTHORITY (in our case, it was XAUTHORITY).
Also, as administrators and security teams work to patch all affected systems, path administrators can temporarily mitigate the vulnerability by removing the setuid permission from the pkexec binary.
The likelihood that attackers will abuse and exploit this vulnerability is high. Given the number of proofs that came about from when it was disclosed, it will only be a matter of time before attackers include an exploit for this gap in their campaigns and attack arsenal. All major Linux distributors, such as RedHat, Debian, Ubuntu, CentOS, and Suse, are considered vulnerable; hopefully, fixes for these distributions can be released soon.
This vulnerability can be used in any environment in which attackers have already established a foothold, from cryptomining and malware infections, to cyberespionage. As stated by the security researchers themselves, it is considered easy, provides root privileges to the attacker, can be used for lateral movement, and is exploitable even if the polkit daemon itself is not running. One silver lining to this vulnerability is that, at its simplest execution, the use of the techniques leaves activity traces in the logs. However, as the security researchers mentioned in their security advisory, there are still ways to exploit this vulnerability without leaving any traces in the auth.log. Security teams are advised to apply the necessary patches as soon as possible, and to enable all applicable solutions for detecting and blocking abuse.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

